Download Cybersecurity Infographics
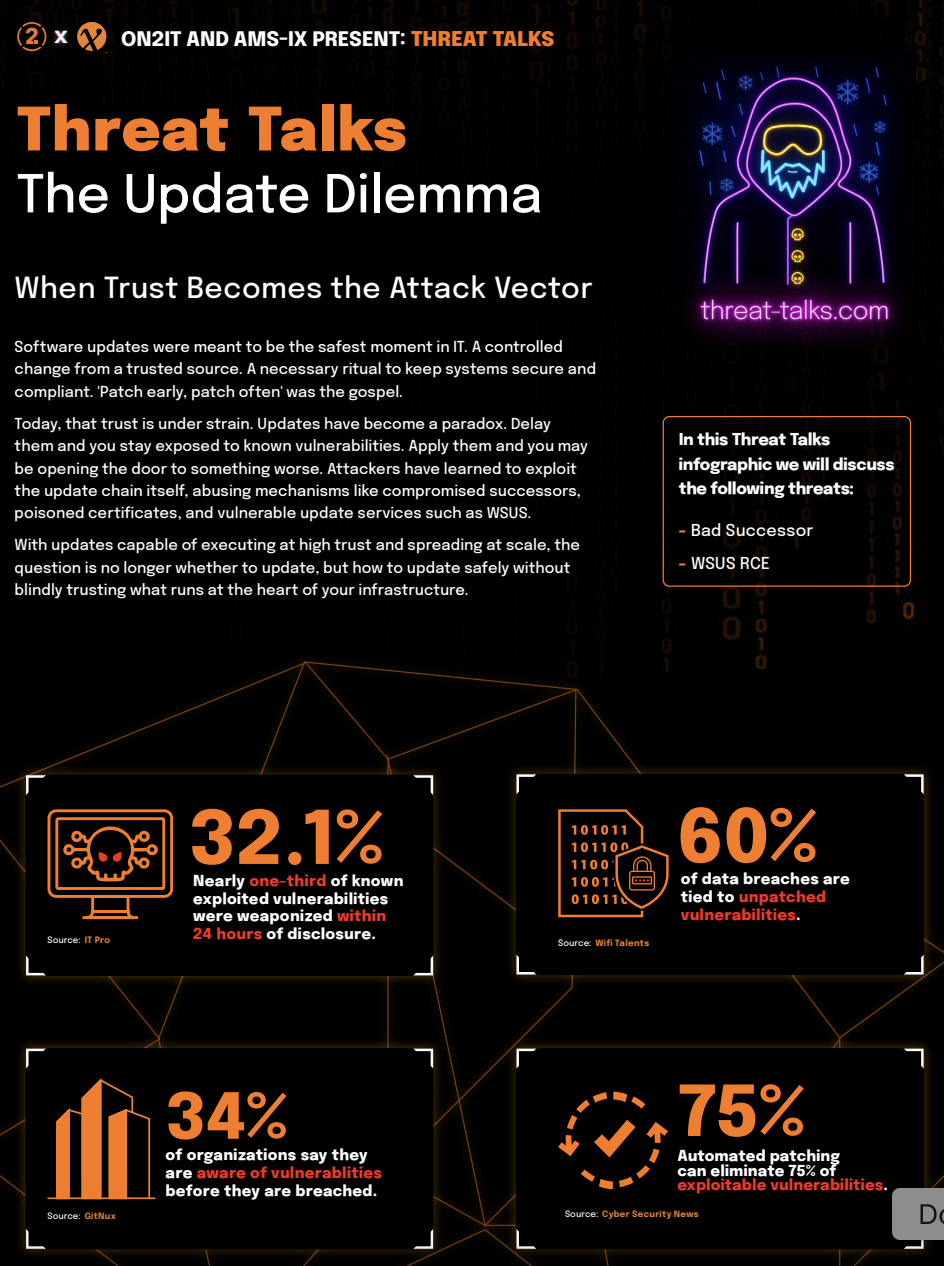
The Update Dilemma
When Trust Becomes the Attack Vector
The Update Dilemma
When Trust Becomes the Attack Vector
The Update Dilemma
When Trust Becomes the Attack Vector
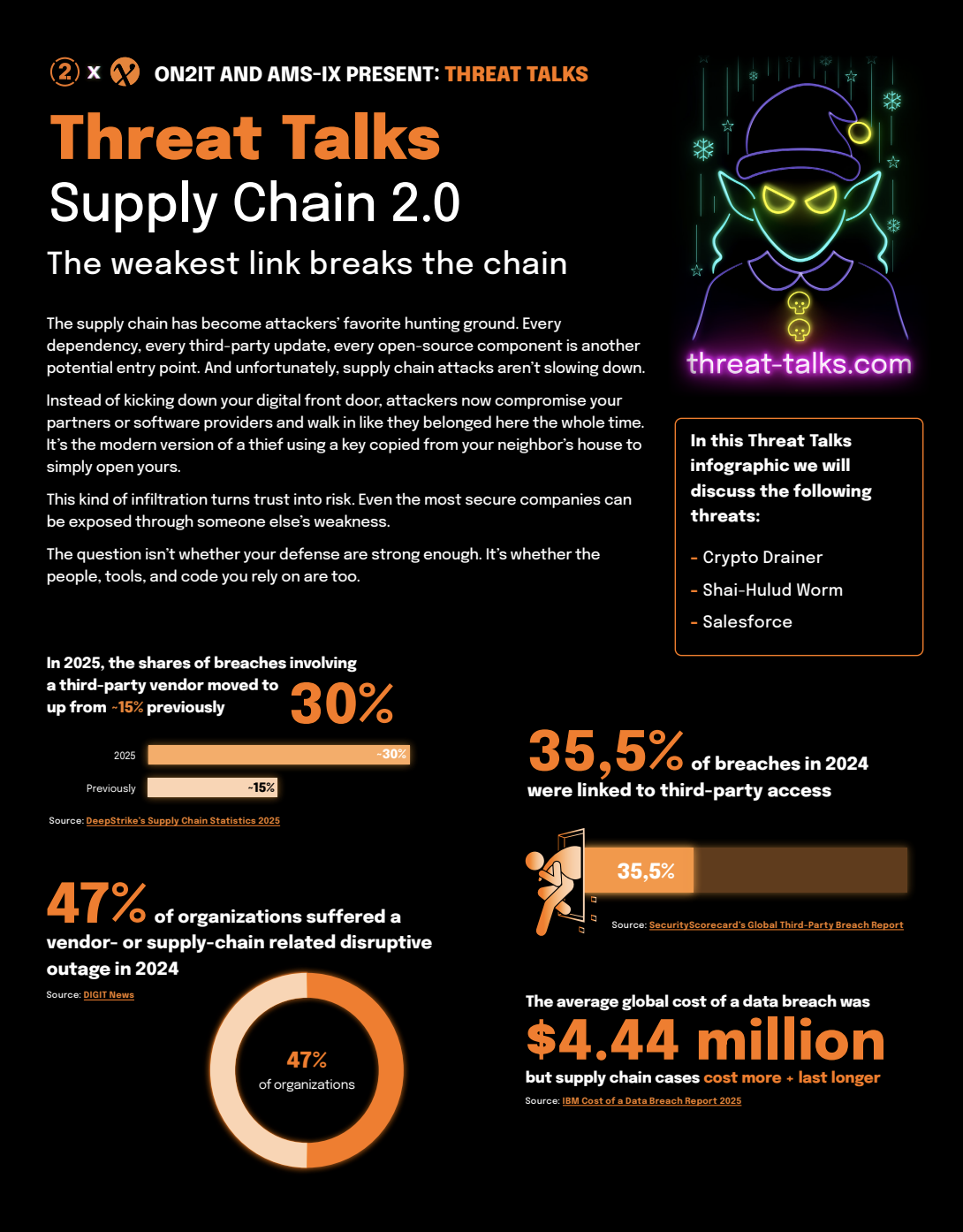
Supply Chain
The weakest link breaks the chain
The supply chain has become attackers’ favorite hunting ground. Every dependency, every third-party update, every open-source component is another potential entry point. And unfortunately, supply chain attacks aren’t slowing down.
Instead of kicking down your digital front door, attackers now compromise your partners or software providers and walk in like they belonged here the whole time. It’s the modern version of a thief using a key copied from your neighbor’s house to simply open yours.
This kind of infiltration turns trust into risk. Even the most secure companies can be exposed through someone else’s weakness.
The question isn’t whether your defense are strong enough. It’s whether the people, tools, and code you rely on are too.
AI-Powered Cyber Threats
The new frontier of cybercrime and defense
In the age of AI, cyber threats have evolved from simple malware to sophisticated, self-learning attacks. AI-powered cyberattacks can adapt in real time, bypassing traditional defenses and targeting vulnerabilities with unprecedented precision. These threats are not just theoretical; they’re already here, reshaping the landscape of cybersecurity.
As AI continues to advance, its potential for misuse grows. Cybercriminals are leveraging AI to develop more convincing phishing schemes, automate vulnerability discovery, and even create malware that adapts in real time to bypass security measures. This evolution demands a proactive and adaptive cybersecurity strategy to safeguard against increasingly sophisticated threats.
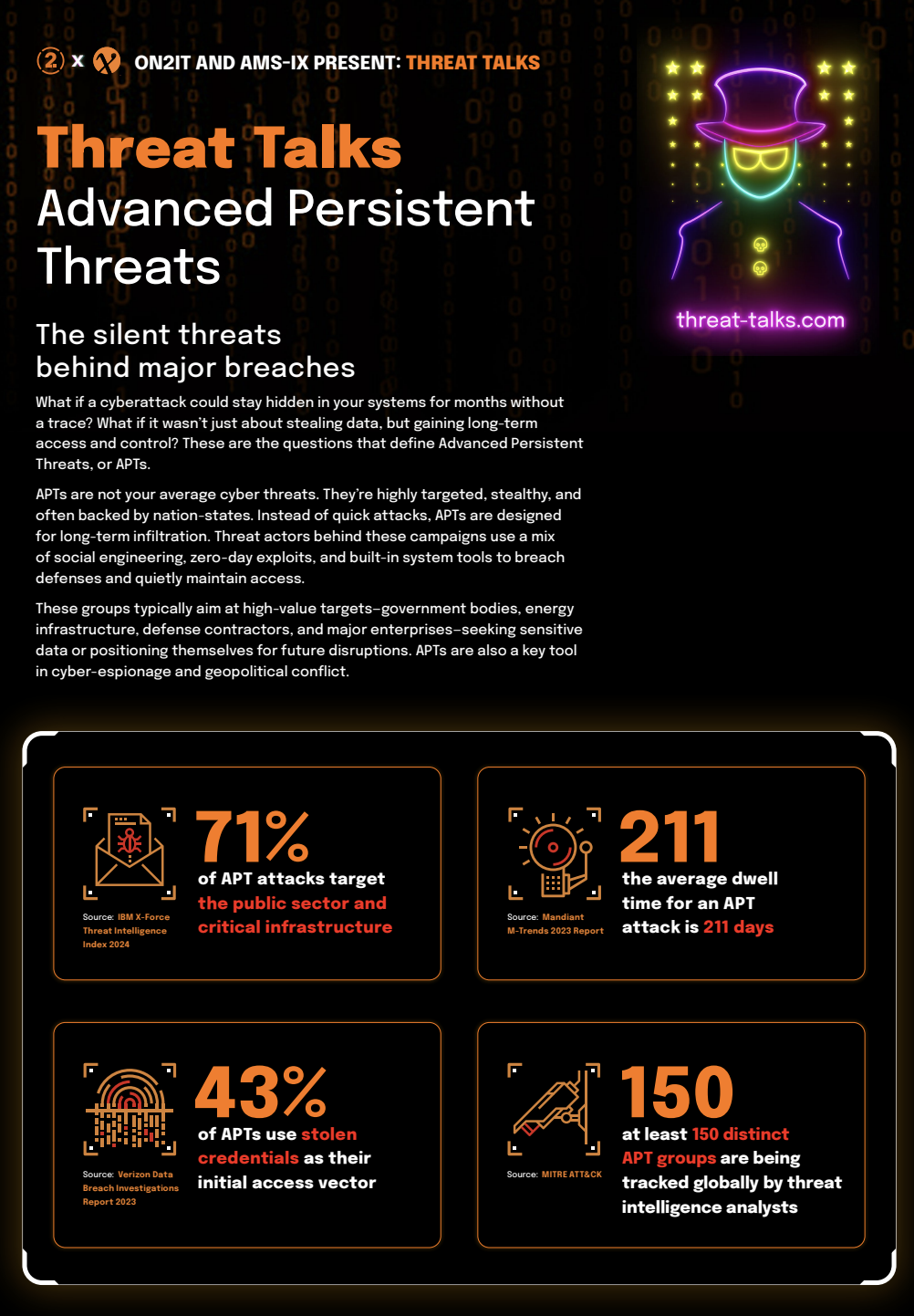
Advanced Persistent Threats
The silent threats behind major breaches
What if a cyberattack could stay hidden in your systems for months without a trace? What if it wasn’t just about stealing data, but gaining long-term access and control? These are the questions that define Advanced Persistent Threats, or APTs.
APTs are not your average cyber threats. They’re highly targeted, stealthy, and often backed by nation-states. Instead of quick attacks, APTs are designed for long-term infiltration. Threat actors behind these campaigns use a mix of social engineering, zero-day exploits, and built-in system tools to breach defenses and quietly maintain access.
These groups typically aim at high-value targets—government bodies, energy infrastructure, defense contractors, and major enterprises—seeking sensitive data or positioning themselves for future disruptions. APTs are also a key tool in cyber-espionage and geopolitical conflict.
Data Exfiltration
How attackers extract sensitive data from your environment
Data exfiltration is the unauthorized transfer of data from a network, typically after an attacker has already gained access. It’s a common goal in many cyber incidents, whether the motive is financial, strategic, or political.
Attackers often use legitimate channels to move data, including HTTPS, FTP, and cloud apps, which helps them avoid detection. In more advanced operations, they may obfuscate stolen data within other network traffic or split it into chunks to avoid triggering security tools. In 2020, cybercriminals exfiltrated hundreds of millions of customer records from Microsoft and Facebook alone. For individuals, data that is stolen through exfiltration can result in costly consequences such as identity theft, credit card or bank fraud and blackmail or extortion. For organizations, the consequences are at the very least more costly, ranging from disrupted operations to compromised trade secrets, and loss of customer trust to regulatory fines.
If attackers were inside your network right now, would you know? How long could they stay hidden? Could your systems catch the signs of data slipping out in real time?
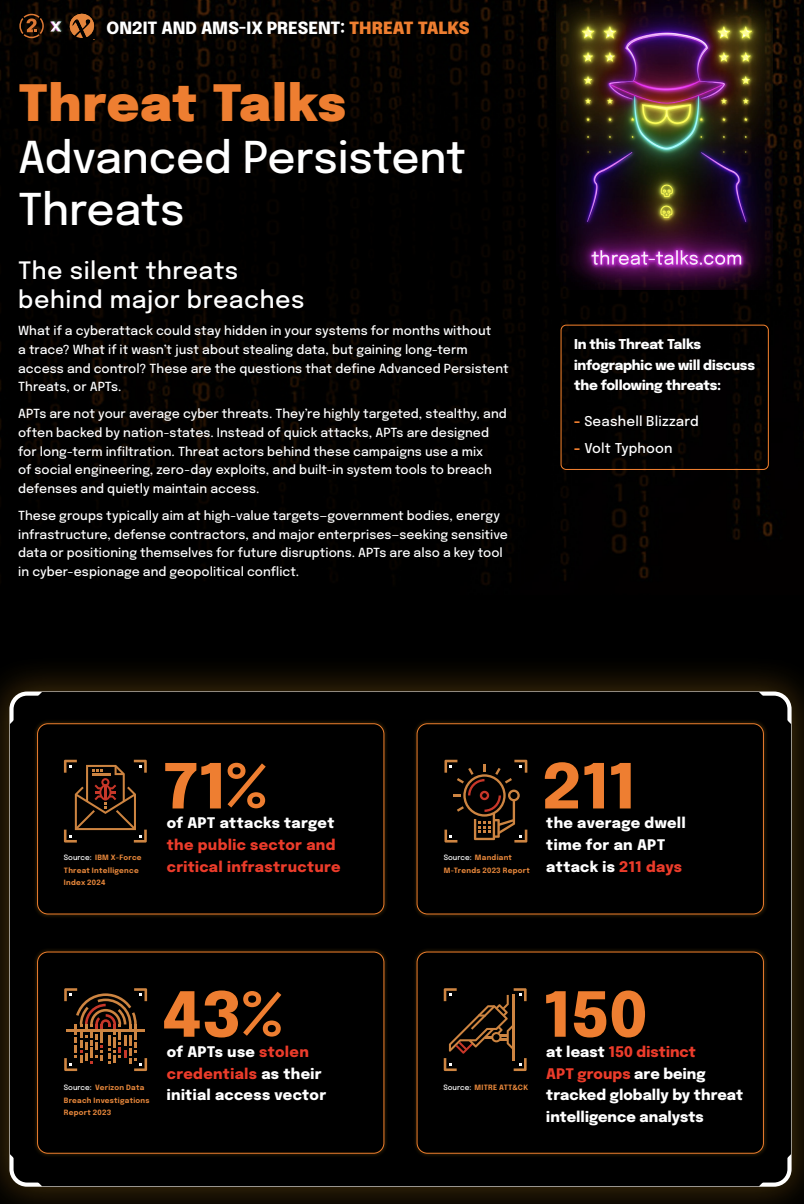
Advanced Persistent Threats
The silent threats behind major breaches
What if a cyberattack could stay hidden in your systems for months without a trace? What if it wasn’t just about stealing data, but gaining long-term access and control? These are the questions that define Advanced Persistent Threats, or APTs.
APTs are not your average cyber threats. They’re highly targeted, stealthy, and often backed by nation-states. Instead of quick attacks, APTs are designed for long-term infiltration. Threat actors behind these campaigns use a mix of social engineering, zero-day exploits, and built-in system tools to breach defenses and quietly maintain access.
These groups typically aim at high-value targets—government bodies, energy infrastructure, defense contractors, and major enterprises—seeking sensitive data or positioning themselves for future disruptions. APTs are also a key tool in cyber-espionage and geopolitical conflict.
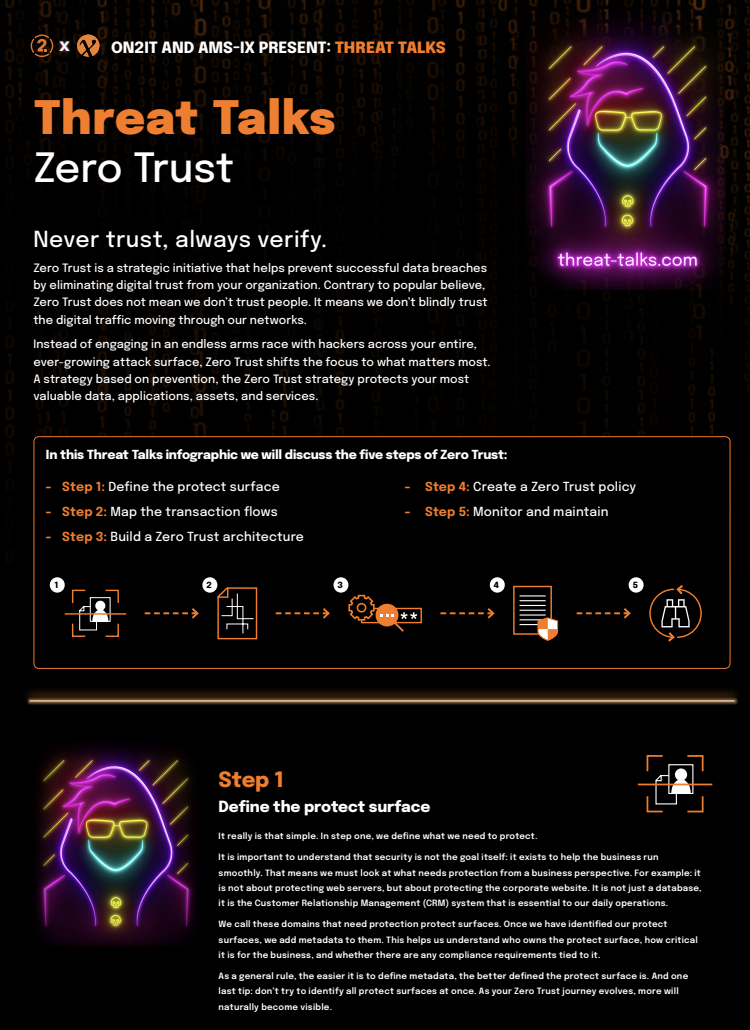
Zero Trust
Never trust, always verify
Zero Trust is a strategic initiative that helps prevent successful data breaches by eliminating digital trust from your organization. Contrary to popular believe, Zero Trust does not mean we don’t trust people. It means we don’t blindly trust the digital traffic moving through our networks. Instead of engaging in an endless arms race with hackers across your entire, ever-growing attack surface, Zero Trust shifts the focus to what matters most. A strategy based on prevention, the Zero Trust strategy protects your most valuable data, applications, assets, and services.
Hackers’ Toolbox
What hackers use and how to counter it
purposes.
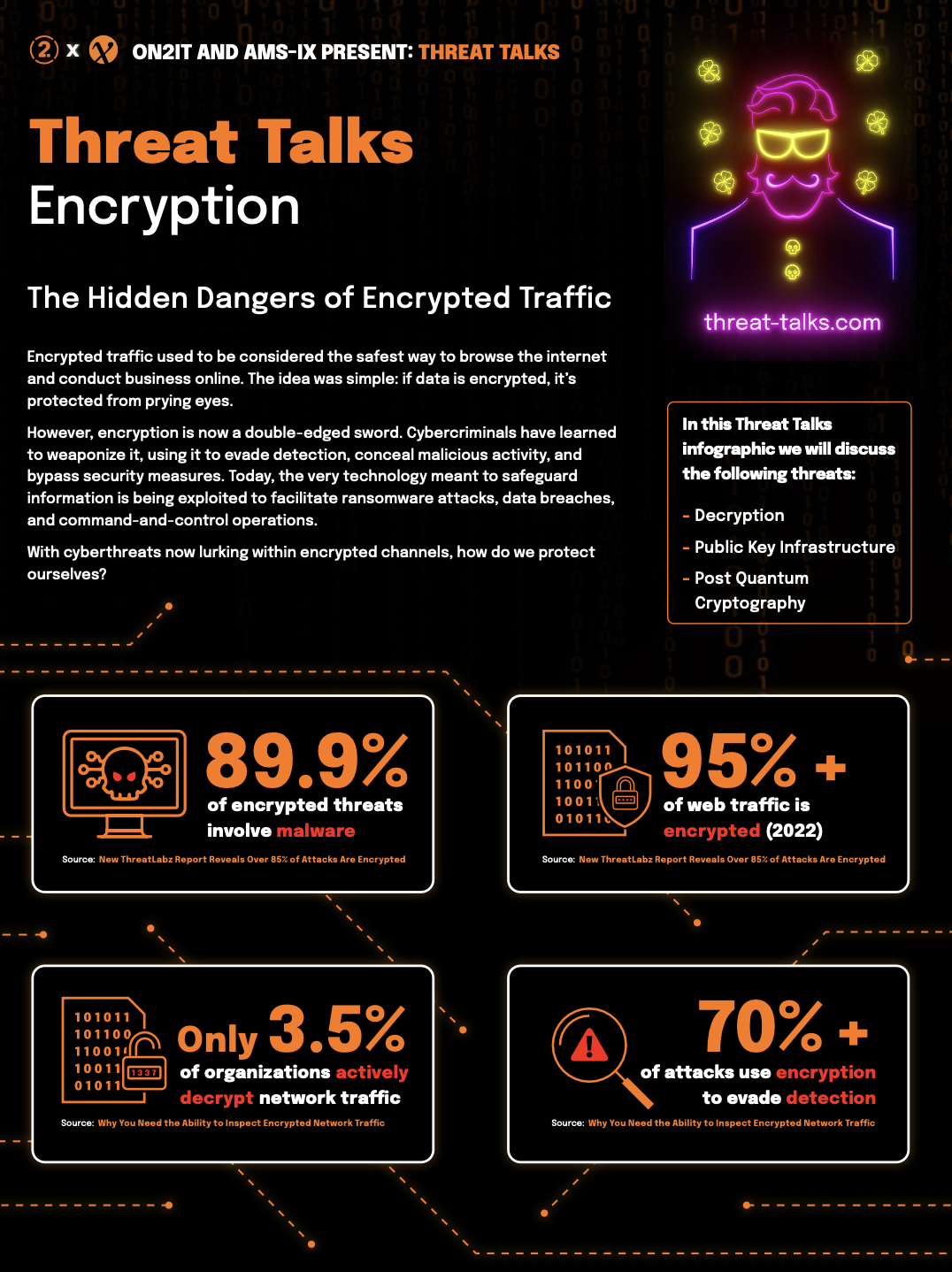
Encryption
The Hidden Dangers of Encrypted Traffic
Encrypted traffic used to be considered the safest way to browse the internet and conduct business online. The idea was simple: if data is encrypted, it’s protected from prying eyes.
However, encryption is now a double-edged sword. Cybercriminals have learned to weaponize it, using it to evade detection, conceal malicious activity, and bypass security measures. Today, the very technology meant to safeguard information is being exploited to facilitate ransomware attacks, data breaches, and command-and-control operations.
Don’t miss out on this dynamic discussion between Jeroen Scheerder and Rob Mass from ON2IT as we discuss the following threats:
- Decryption
- Public Key Infrastructure
- Post Quantum Cryptography
Prevent, Pay or Insure
The Road to Cyber Resilience
Days before MGM’s computer systems were taken down in a cyberattack, fellow casino operator Caesars paid a $15 million ransom to attackers who infiltrated its systems.
MGM chose not to pay and dealt with different costs because of it – did the two casino giants wind up paying similar amounts down the line? And what role does cybersecurity insurance play in these scenarios?
Don’t miss out on this dynamic discussion with Davis Hake as we explore how organizations can better prepare for and respond to ransomware incidents:
- MGM Resorts Ransomware Attack
- Conti Ransomware Attack on Costarican Government
- Dutch Law Enforcement Data Outleak
Breaking the Illusion
Confronting Cybersecurity’s Biggest Fallacies
Are we truly protecting ourselves from cyber threats, or are we blinded by outdated security practices? In this Threat Talk, ON2IT’s Lieuwe Jan Koning sits down with cybersecurity experts Fleur van Leusden, CISO and host of the Dutch podcast ‘CISO Praat’, and Jeroen Scheerder for an in depth discussion on the challenges and misconceptions shaping cybersecurity today.
Don’t miss out on this dynamic discussion as we rethink traditional approaches and uncover the hidden vulnerabilities shaping today’s cybersecurity scene as:
- The CrowdStrike auto-update disaster
- Backdoor vulnerability in XZ Utils (CVE-2024-3094)
- UNIX CUPS
Hack the Boat
Explore the cutting-edge of maritime cybersecurity
For years, maritime companies have focused on protecting their data and IT environments, but securing operational technology (OT) was less of a priority. One reason for this is that, until recently, said operational systems simply weren’t connected to the internet. Modern shipping operations however rely heavily on both Information Technology (IT) and Operational Technology (OT) for navigation, communication, and operational management. Especially the conventional OT systems, which have been built with fairly open and unencrypted, sometimes decades old systems, are like an open invitation to hackers.
With marine cybercrime steeply on the rise, what can maritime companies do to bring their IT and OT in line with today’s cybersecurity standards?
In this Threat Talk, the following key threats are discussed:
- Ballast system hack
- Securing AIS
Bridging the Gap: Security and Compliance
What’s more important: compliance or cybersecurity?
Explore the often-overlooked operational gap between compliance and actual security in episode #33 of Threat Talks. While many organizations focus on meeting compliance standards, does this truly lead to enhanced security?
Is compliance the be-all-end-all when it comes to cybersecurity? Or is there a bridge we need to gap when it comes to compliance versus practical cybersecurity requirements? Join us as we delve into the critical differences and uncover how to bridge the gap for better protection.
In this Threat Talk, the following key threats are discussed:
- Accellion file transfer
- OKTA data breach
- CapitalOne data breach
The Evolution of Cyber Warfare
Advanced Threat Intelligence helps you know your enemy
Explore the hidden world of cyber warfare and Advanced Persistent Threats (APT’s) with Threat Intel Specialist Luca Cipriano and special guest Cyber Security Expert Martijn Peijer as they unpack real-life cyber espionage cases.
Host Lieuwe Jan Koning discusses real-life espionage cases like:
- China Nexus Barracuda Hack
- Russia GRU Viasat Hack
- APT Sand Eagle – Operation Triangulation
Breaking the Bank
Financial sector cybersecurity threats
Discover the intriguing world of legal bank heists with special guest and cybersecurity expert Jayson E Street. Lieuwe Jan Koning and Luca Cipriano delve into how Jayson exploits human nature to breach bank security, bypassing technology with ease.
Understand the critical importance of employee training in safeguarding against cyber threats. Explore ethical hacking, data theft, and the fascinating dynamics of modern cybersecurity.
In this Threat Talk, we’re delving into three major vulnerabilities:
- SWIFT Gateway vulnerability
- Android banking malware known as Vultur
- Binance crypto hack
Healthcare
Responsibilities, regulations and legacies
Explore the vulnerabilities of the DICOM protocol in healthcare, revealing significant risks such as data breaches and manipulation.
Join host Lieuwe Jan Koning and guests Jan van Boesschoten and Sina Yazdanmehr as they discuss practical solutions for protecting sensitive patient information and enhancing cybersecurity measures.
In this Threat Talk, the following key threats are discussed:
- DICOM: The hidden risks of Legacy Protocols
- Ireland’s HSE Ransomware Attack
- ScreenConnect: Authentication Bypass (CVE-2024-1709)
Unraveling CVE-2024-3400
Threat Talks Special
In this special episode of Threat Talks, the focus is on the critical vulnerabilities found in Palo Alto Networks’ GlobalProtect servers, particularly CVE-2024-3400 with a CVSS score of 10. The discussion covers the nature of this severe vulnerability, how it was discovered, and the risks it poses to organizations using GlobalProtect.
You will learn about the methods attackers might use to exploit this vulnerability and practical steps to protect against such threats. The episode provides straightforward advice and recommendations to help organizations improve their security measures and safeguard their networks from similar vulnerabilities.
Supply Chain
Business as usual?
As we increasingly depend on third-party and open-source software, the threat of supply chain attacks escalates. These attacks occur when hackers find and exploit less direct routes into systems, akin to burglars gaining entry with a hidden spare key.
Lieuwe Jan, Luca, and Matthijs delve into several significant hacks:
- SolarWinds: Highlighting the risks associated with third-party software.
- Log4j: Underlining the perils of software dependencies.
- MOVEit: Pointing out the risks involved when entrusting data to third-party software.
The Authentication Apocalypse
Staying Ahead of the Hacker
Word of data breaches and stolen credentials reaches the news almost every other day. If your credentials get stolen, criminals could have access to your bank accounts, health care records, company secrets and more. Needless to say, authentication is key!
At its core, authentication verifies the identity of users seeking access to various digital services and platforms.
In this episode, Lieuwe Jan, Luca and Harald discuss the following hacks:
- Outlook vulnerability
- Google Oauth bypass
- Ivanti EPM
Does Remote Work?
Vulnerabilities at home
Allowing remote access, whether it is for remote workers or partners, is required for almost all enterprises. But enabling remote access doesn’t just bring flexibility, it comes with a number of security concerns.
Cybercriminals have honed in on the vulnerabilities of widely used remote work technologies. What are those technologies and what are those vulnerabilities? For example: the FBI and NSA talk about rebooting your home router at least every week. Should we do this?
The following threats will be discussed by Lieuwe Jan, Luca and Rob:
- Citrix Netscaler
- TunnelCrack
- FortiOS SSLVPN buffer overflow
Can’t deny DDoS in 2024?
Distributed-denial-of-service attacks
Distributed-denial-of-service attacks, more commonly referred to as DDOS attacks, are malicious attempts to disrupt traffic of a specific server, service or network by overwhelming said target or its surroundings with an abundance of internet traffic.
Think of it as an unexpected traffic jam clogging up the highway, preventing regular traffic from arriving at its destination. Want to know how often these attacks really take place? Download the infographics on DDoS attacks in general.
Lieuwe Jan, Peter and Luca are talking about these threats:
- Mirai botnet
- HTTP/2 rapid reset
- Reflection and Amplification DDoS attacks.